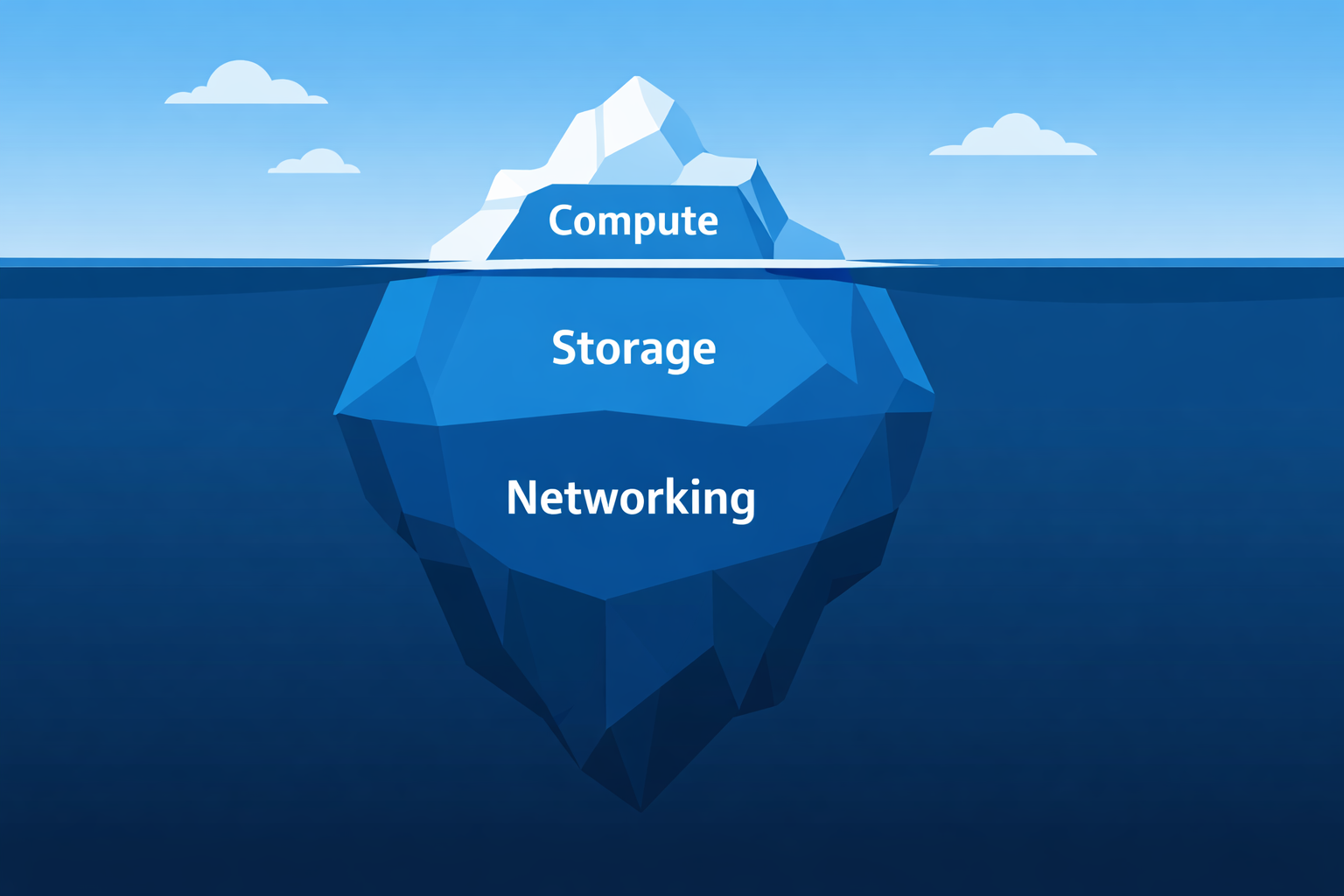
The Three Layers of Kubernetes Cost Waste Most Teams Miss
This is article 1 in a series about Kubernetes cost optimization. I explore how cost waste hides across compute, storage, and networking. More importantly, I will explore how to tackle it with automation instead of manual audits. A team right-sizes their deployments very well, and cuts compute costs by 30%. Then someone looks at the rest of the bill and starts investigating. Dozens of volumes and disks sitting unattached. Load balancers fronting services with 2 requests per hour. An entire development environment running 24/7 with no activity for the last 3 days. The compute cuts they celebrated? A fraction of the total waste. ...

Native support for Kubernetes Network Policies on EKS
Introduction When a new Kubernetes cluster is created, there is no isolation between pods running on that cluster. All pods are allowed to communicate with each other and the outside. To control traffic between the different workloads and external services, Kubernetes provides the NetworkPolicy objects. Network Policies are native Kubernetes objects to define these isolation rules. Why Network Policies? One way of viewing a Kubernetes cluster is a platform that is capable of hosting different heterogeneous workloads and managing them on this same platform. These workloads may be developed by different teams from the same organization, or even by a third party from outside the organization. ...

Kubernetes Readiness, Liveness and Startup Probes
Introduction As a container orchestrator, Kubernetes manages the lifecycle of containers in a cluster. The kubelet will ensure that the containers of the different pods are running and healthy. These pods (podSpec) are provided through the apiserver. Different probes are used by the kubelet to decide how to treat a container and what actions to take. We can use each of these probes to achieve an optimal experience when running our containers. ...

Let's Encrypt and cert-manager: Securing Kubernetes Services
Introduction Kubernetes is becoming more and more popular these recent years. Many new projects choose it - by default - as a platform. Its flexibility and advantages are numerous to the point that many of the legacy applications are getting refactored, containerized, and migrated to Kubernetes. In real life, it is common to have services you develop and maintain, and third-party services and tools, deployed altogether in the same cluster (or clusters). ...

Certificates: Kubernetes to AWS Certificate Manager Sync
Introduction Nowadays, Kubernetes has become the de facto platform to run and manage containerized applications and services. On the other hand, cloud providers provide a rich catalog of managed services, ready to use. Kubernetes services and managed services are often used in conjunction to build a product or service. A security pilar is to make sure communications are secure between services, and for exposed endpoints. One of the first step to achieve this is using TLS Certificates for communication. ...